Synchronizing AI, Cloud, and Cybersecurity Excellence
An increasingly complex world presents systemic challenges that AI can help solve.
Digital Trust Infrastructure is critical to our individual, community, national, and world security.
The Synthesis of Software-Hardware-Wetware will determine our civilization’s future.
POLYKEY
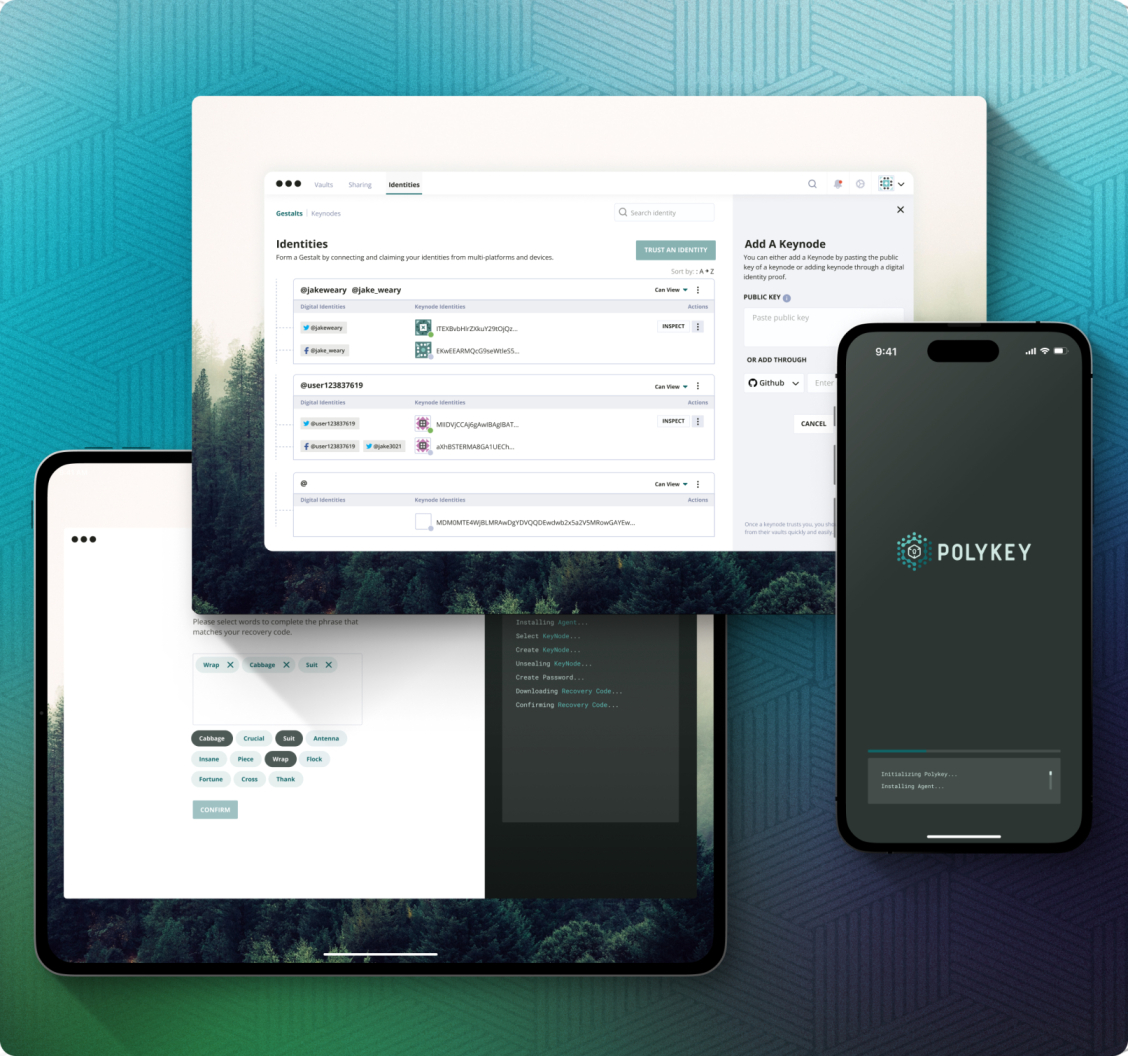
Decentralized Zero Trust for Secrets Management for Cyber-Physical Infrastructure
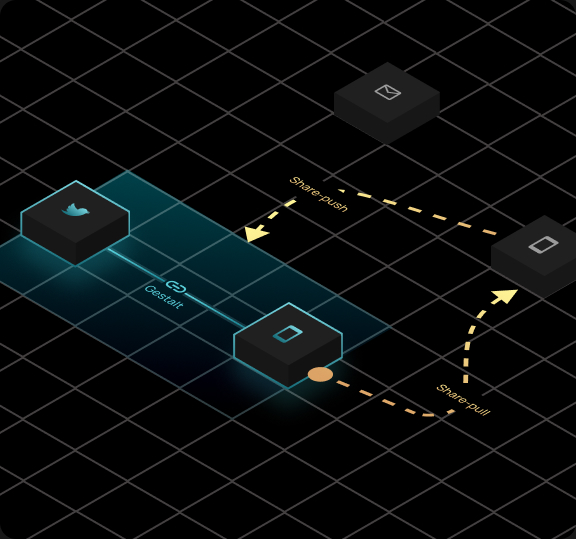
The Polykey platform helps individuals and organisations manage cybersecurity risks, by providing a platform for zero trust workflows. "SecretOps"
POLYKEY ENTERPRISE
Secrets Management for Cyberphysical Infrastructure
Polykey Enterprise builds on top of Polykey, an open-source decentralized secret sharing system.
MATRIX OS
Configuration Orchestration for Cloud, AI and IoT workloads
Matrix OS is an operating system designed for the next era of cloud and internet of things. Its primary objective is to orchestrate massive distributed infrastructure so that they become self-healing, self-organising, and self-adaptable.
START HERE
Artificial Intelligence
Digital Trust
LATEST ARTICLES
PRESENTATIONS
EVENTS
Jan 23, 2023
00:00
Our Cybersecurity and Digital Trust Community
Apart from our professional endeavours, we're also committed to building a